Yearlong supply-chain attack targeting security pros steals 390K credentials
But wait, there’s more
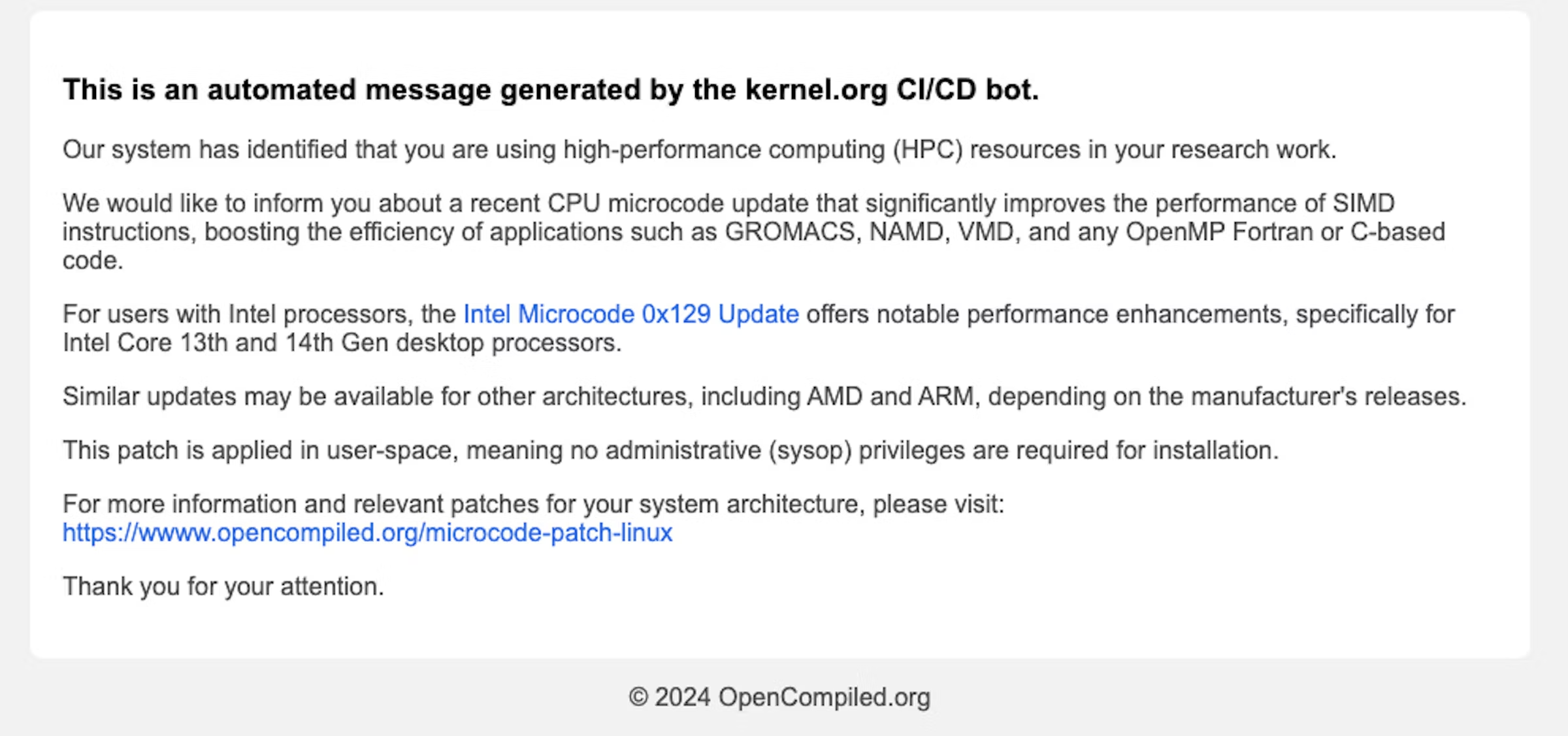
On Friday, Datadog revealed that MUT-1244 employed additional means for installing its second-stage malware. One was through a collection of at least 49 malicious entries posted to GitHub that contained Trojanized proof-of-concept exploits for security vulnerabilities. These packages help malicious and benevolent security personnel better understand the extent of vulnerabilities, including how they can be exploited or patched in real-life environments.
A second major vector for spreading @0xengine/xmlrpc was through phishing emails. Datadog discovered MUT-1244 had left a phishing template, accompanied by 2,758 email addresses scraped from arXiv, a site frequented by professional and academic researchers.
- Top 18 Best Web Hosting Services In 2024: Despite there are multiple web hosting providers available in the market, choosing the best one is really a hard nut to crack!! Because almost all service providers are offering their services with the same features and quality.
- How to start your own Crypto currency website: For a cryptocurrency news website, choosing the right Content Management System (CMS) is crucial for managing content effectively, ensuring security, and providing a great user experience. Here are some of the best CMS options tailored for such a site, each with its unique strengths:
- The Evolution of Coffee Brewing Methods: A Historical Perspective: Coffee has been brewed and enjoyed for centuries, with various methods evolving over time to create the perfect cup of joe. From early methods like the Ibrik method and coffee pots for coffee houses to modern technologies like the AeroPress and Hario V60, the world of coffee brewing has come a long way.
- Stop WordPress from Creating Extra Cropped Image Sizes: Whenever you upload an image to your WordPress site through the media library, it automatically creates and stores multiple additional versions of that image. If your site doesn’t utilize these extra image sizes, they will consume valuable storage space and increase the size of your server backups.
- Explain WordPress Portfolio and how to created them: WordPress portfolios are digital showcases for individuals or businesses to display their work, projects, or professional accomplishments. This feature is particularly useful for creatives, freelancers, and agencies looking to exhibit their skills or services in a visually appealing and organized manner. Portfolios in WordPress can be created using various methods, including themes that come with built-in portfolio functionalities, plugins that add portfolio features, or custom coding for a more personalized approach.
- 15 Essential WordPress Plugins For Every Site: Plugins are essential for every type of website, as they provide additional features and customization options that are not available in the core WordPress platform. A study by CodeinWP found that the average WordPress site has 20 active plugins, indicating the importance of plugins in website development.
- SAILING and YACHTING: Awesome Sailing Vlogs for the Enthusiast
- Comparing Google and Microsoft’s Success in Capitalizing on Generative AI: The buzz of interest in AI services helped drive revenue for Microsoft’s biggest unit, cloud services—up by 7 percentage points compared to a year ago—and Microsoft’s overall sales rose 17 percent to nearly $62 billion. It also gained cloud market share, Nadella added. The number of $100 million cloud deals that Microsoft landed increased 80 percent during the quarter compared to the same period a year ago, and $10 million deals doubled.
- The Best WordPress Hosting Solution in Australia: Each of our WordPress hosting solutions are fine-tuned, blazing fast and are ready for you! Starting a WordPress website has never been easier with our free 1-click WordPress installation, enterprise-grade security and an assortment of tutorials and helpful guides to get you started, all backed by our 99.9% uptime guarantee.
- Elementor vs Beaver Builder: A Comparison of Design Flexibility and Performance in WordPress: Elementor and Beaver Builder are two of the most widely recognized options, each providing distinct features that cater to varying user requirements. This article conducts a comprehensive comparison of these tools, examining their design flexibility, performance metrics, and overall user experience.
- The Best Contact Form Plugins for WordPress to Easily Manage User Inquiries: In an effort to improve user interactions on WordPress websites hosting, the examination of contact form plugins becomes essential. This article aims to present an overview of the top 5 contact form plugins available for WordPress, highlighting their features and pricing structures to facilitate an well-considered choices process.
- What are the 20 best Joomla plugins: Joomla plugins are small, task-specific extensions that enhance or modify the core functionality of a Joomla website. They operate as event-driven scripts, listening for specific “events” triggered by Joomla or its components and executing corresponding actions. Plugins are a crucial part of Joomla’s extensibility, allowing developers to add features or customise behaviour without altering the core Joomla code.
- How to design a strong off-page SEO strategy: Lessons learnt from earning over 50,000 contextual links for thousands of websites in the toughest niches. In 2023, virtually every business that has a website is prioritizing their investment in SEO. The reason being, amidst the chaos of the current year, customers are resorting to online channels for safe purchasing, and optimizing their online presence is a surefire way to gain an edge over rivals. While some firms have set up internal teams, and others have hired external agencies to boost their search engine rankings, a documented off-page SEO strategy is still a rarity among most businesses.
- What are WordPress Plugins? WordPress plugins are modular pieces of software that can be added to a WordPress site to extend or enhance its functionality without modifying the core WordPress code. They allow website owners to add features, improve performance, and customise the behaviour of their websites easily, catering to a wide range of needs, from SEO and security to e-commerce and design enhancements.
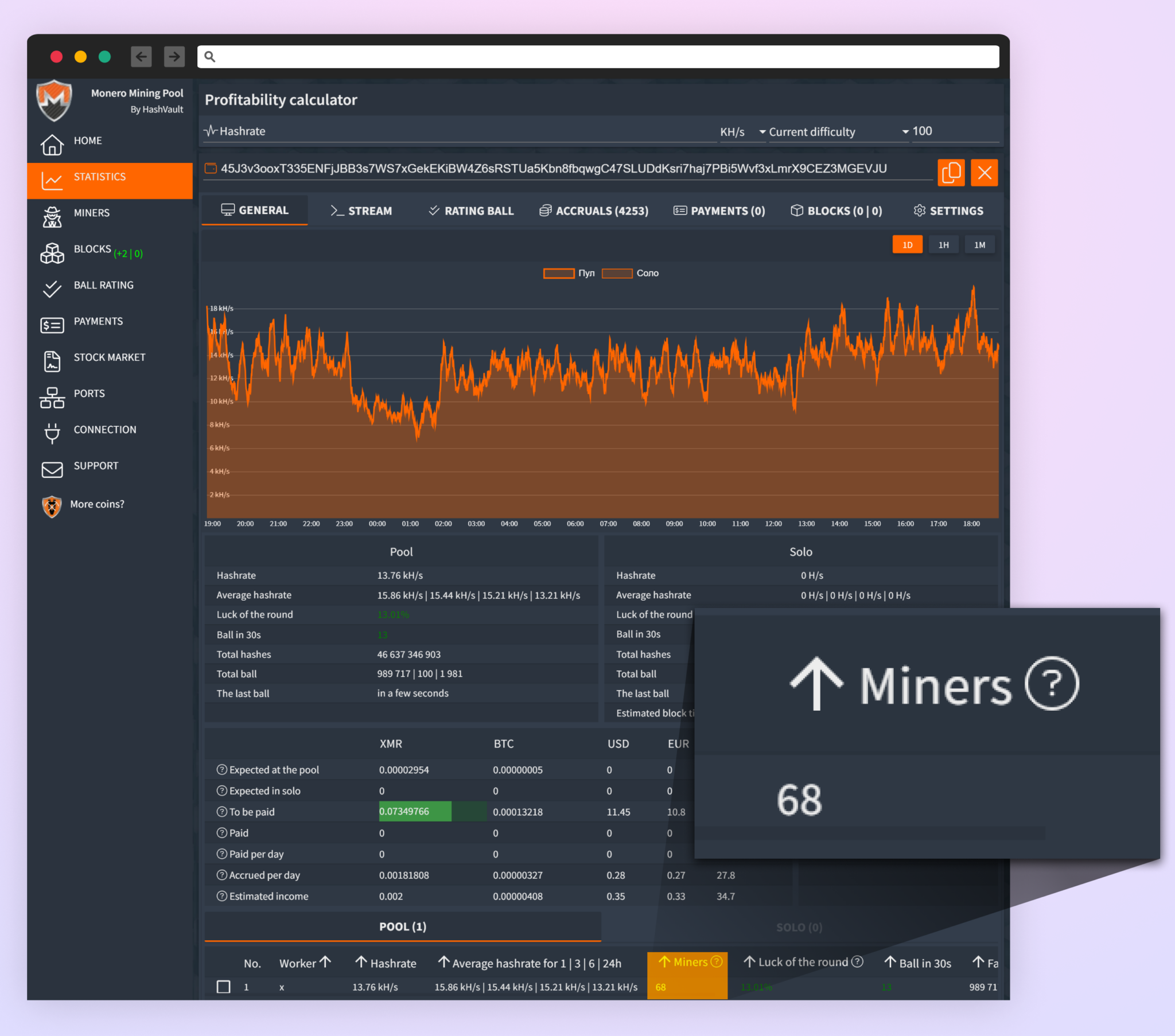
A phishing email used in the campaign.
Credit:
Datadog
The email, directed to people who develop or research software for high-performance computing, encouraged them to install a CPU microcode update available that would significantly improve performance. Datadog later determined that the emails had been sent from October 5 through October 21.
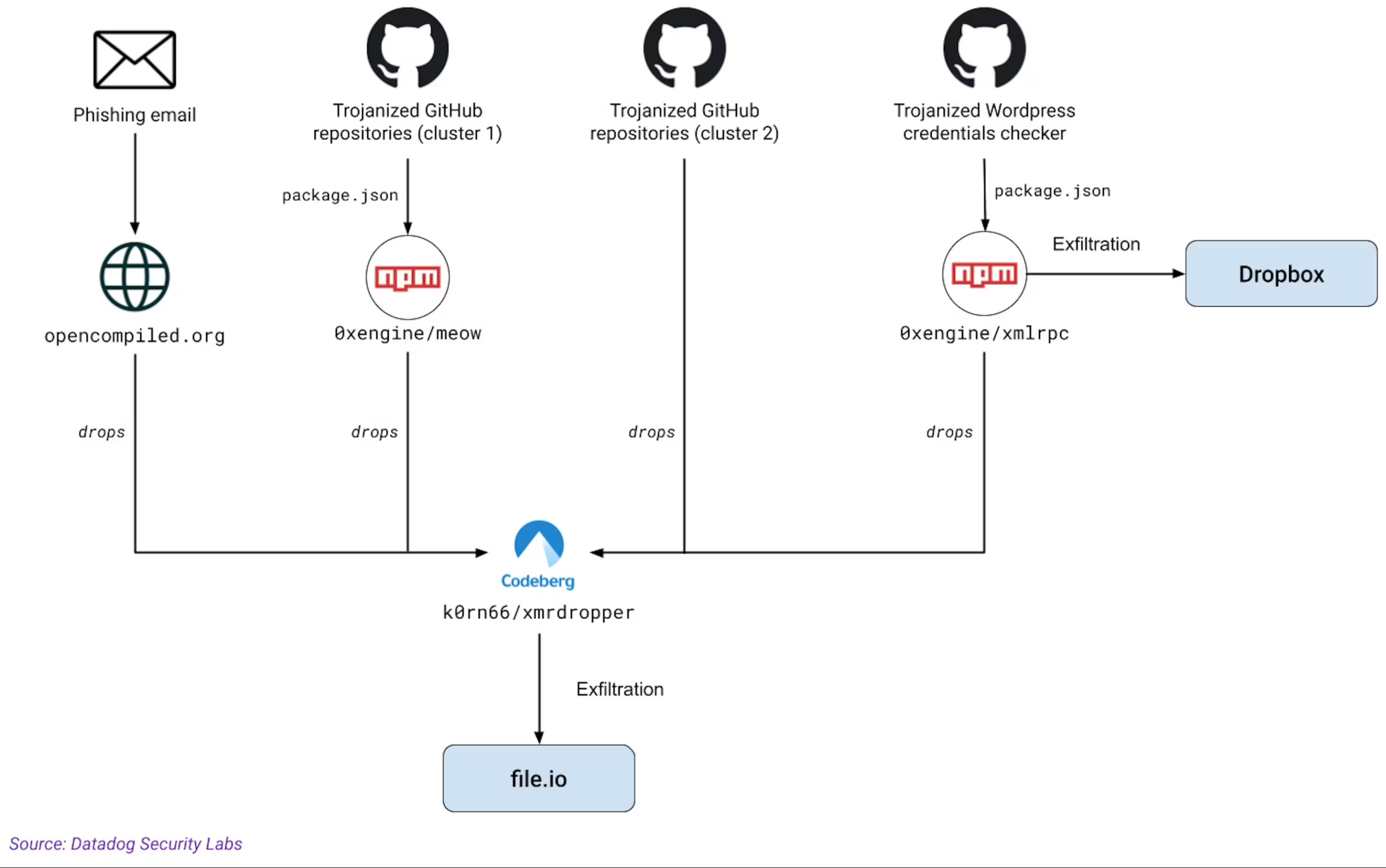
Additional vectors discovered by Datadog.
Credit:
Datadog
Further adding to the impression of legitimacy, several of the malicious packages are automatically included in legitimate sources, such as Feedly Threat Intelligence and Vulnmon. These sites included the malicious packages in proof-of-concept repositories for the vulnerabilities the packages claimed to exploit.
“This increases their look of legitimacy and the likelihood that someone will run them,” Datadog said.
The attackers’ use of @0xengine/xmlrpc allowed them to steal some 390,000 credentials from infected machines. Datadog has determined the credentials were for use in logging into administrative accounts for websites that run the WordPress content management system.
Taken together, the many facets of the campaign—its longevity, its precision, the professional quality of the backdoor, and its multiple infection vectors—indicate that MUT-1244 was a skilled and determined threat actor. The group did, however, err by leaving the phishing email template and addresses in a publicly available account.
The ultimate motives of the attackers remain unclear. If the goal were to mine cryptocurrency, there would likely be better populations than security personnel to target. And if the objective was targeting researchers—as other recently discovered campaigns have done—it’s unclear why MUT-1244 would also employ cryptocurrency mining, an activity that’s often easy to detect.
Reports from both Checkmarx and Datadog include indicators people can use to check if they’ve been targeted.